When properly addressed, security considerations should not be a barrier to an insurer utilizing and realizing the benefits of cloud-based core systems.
As more insurers consider moving some of their core systems to the cloud, many want to know how secure their data and applications will be. This report examines how major cloud providers are addressing security risks.
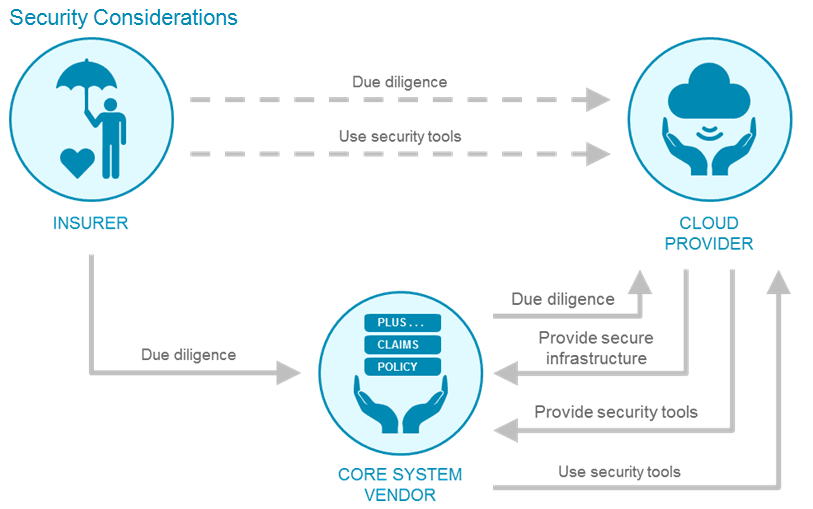
There are four major security considerations for cloud-based core systems: application risks, data risks, intellectual property risks, and physical risks.
There are two basic models for how an insurer can use core systems in the cloud.
- Model One: An insurer licenses core systems from a core system vendor, and then the insurer or an integration partner deploys and uses those core systems in the cloud.
- Model Two: A core system vendor deploys its core systems in the cloud, and then makes those core systems available to an insurer on a subscription basis.
Leading cloud providers create and maintain a set of services and capabilities to provide security for infrastructure and platform cloud elements. The breadth and depth of these tools and capabilities are generally equal to, and often better than, those utilized by individual insurers that deploy core systems on their own premises.